top of page


Understanding the Principles of Ethical AI
Artificial Intelligence (AI) has rapidly evolved from futuristic curiosity to everyday reality. From personalized healthcare to predictive policing, AI influences how we live, work and interact. But as its impact grows, so do the ethical dilemmas it brings. How do we ensure that algorithms treat people fairly? Who takes responsibility when an autonomous system makes a harmful decision? Ethical AI refers to the responsible design, development and deployment of artificial int
sujosutech
Oct 31, 20254 min read


Implementing an Effective Grievance Redressal Mechanism under the DPDP Act, 2023
India’s Digital Personal Data Protection Act (DPDP), 2023 marks a turning point in how organizations handle personal data. For the first time, Indian citizens are being given enforceable digital rights; and at the heart of those rights lies a simple but powerful expectation: “If my data has been mishandled, I have the right to be heard, and to be redressed.” That expectation will be operationalized through the Grievance Redressal Mechanism that will serve as the bridge bet
sujosutech
Oct 23, 20255 min read

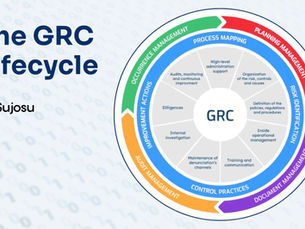
The future of GRC: Governance as Code
Governance as code is a modern way of managing policies and compliance by treating them as code. Unlike traditional governance, which...
sujosutech
Sep 18, 20254 min read


Beyond the Hype: Securing Your Enterprise AI with the Model Context Protocol
The AI Revolution Is Here But So Are the Risks AI is no longer a curiosity on the fringes of enterprise IT. It’s in the boardroom, the...
sujosutech
Sep 15, 20256 min read


No-Code Workflow Automation Tools: Empowering Enterprise Efficiency
In today's competitive business environment, enterprises are under constant pressure to accelerate outcomes, enhance security, and...
sujosutech
Sep 9, 20254 min read

Series: Additional Controls in ISO/IEC 27019:2024 for Energy Utilities
Technological Controls – Part III The second edition of the information security standard ISO/IEC 27019:2024 enhances the controls of...
sujosutech
Sep 8, 20253 min read


Best coding practice with Designing High-Performance, Optimized code
In the world of software development, it becomes critical to ensure that your code is not only functional but also efficient,...
sujosutech
Sep 5, 20253 min read


Series: Additional Controls in ISO/IEC 27019:2024 for Energy Utilities
Technological Controls – Part II The second edition of the information security standard ISO/IEC 27019:2024 enhances the controls of...
sujosutech
Sep 2, 20253 min read

Series: Additional Controls in ISO/IEC 27019:2024 for Energy Utilities
Technological Controls – Part I The second edition of the information security standard ISO/IEC 27019:2024 enhances the controls of...
sujosutech
Aug 28, 20253 min read


Series: Additional Controls in ISO/IEC 27019:2024 for Energy Utilities
Physical Controls – Part II The second edition of the information security standard ISO/IEC 27019:2024 enhances the controls of ISO/IEC...
sujosutech
Aug 26, 20253 min read


Series: Additional Controls in ISO/IEC 27019:2024 for Energy Utilities
Physical Controls – Part I The second edition of the information security standard ISO/IEC 27019:2024 enhances the controls of ISO/IEC...
sujosutech
Aug 22, 20253 min read


Series: Additional Controls in ISO/IEC 27019:2024 for Energy Utilities
Organizational Controls The second edition of the information security standard ISO/IEC 27019:2024 was published in October 2024. It...
sujosutech
Aug 19, 20254 min read


Series: New Controls in ISO/IEC 27001:2022 Annex A
Secure Coding In this article series, we are analyzing the implementation aspects of the 11 new controls of ISO/IEC 27001:2022 Annex A....
sujosutech
Jul 28, 20252 min read


Series: New Controls in ISO/IEC 27001:2022 Annex A
Web Filtering In this article series, we are analyzing the implementation aspects of the 11 new controls of ISO/IEC 27001:2022 Annex A....
sujosutech
Jul 25, 20252 min read


Series: New Controls in ISO/IEC 27001:2022 Annex A
Monitoring Activities In this article series, we are analyzing the implementation aspects of the 11 new controls of ISO/IEC 27001:2022...
sujosutech
Jul 23, 20252 min read


Series: New Controls in ISO/IEC 27001:2022 Annex A
Data Leakage Prevention In this article series, we are analyzing the implementation aspects of the 11 new controls of ISO/IEC 27001:2022...
sujosutech
Jul 21, 20253 min read


Series: New Controls in ISO/IEC 27001:2022 Annex A
Data Masking In this article series, we are analyzing the implementation aspects of the 11 new controls of ISO/IEC 27001:2022 Annex A....
sujosutech
Jul 18, 20252 min read

Series: New Controls in ISO/IEC 27001:2022 Annex A
Information Deletion In this article series, we are analyzing the implementation aspects of the 11 new controls of ISO/IEC 27001:2022...
sujosutech
Jul 16, 20252 min read


Series: New Controls in ISO/IEC 27001:2022 Annex A
Configuration Management In this article series, we are analyzing the implementation aspects of the 11 new controls of ISO/IEC...
sujosutech
Jul 14, 20253 min read


Series: New Controls in ISO/IEC 27001:2022 Annex A
Physical Security Monitoring In this article series, we are analyzing the implementation aspects of the 11 new controls of ISO/IEC...
sujosutech
Jul 10, 20252 min read
bottom of page